Cyber Threat: Latest Computer Viruses & Malware Threats 2020

In a world full of cybercriminals and hackers, protecting your system from the latest computer viruses, malware threats, Trojans, and other network volumetric attacks should be one of your top priorities.
These destructive viruses can easily infiltrate the security vulnerable system without the users’ knowledge and steal sensitive information like IP address, browser history, username, passwords, banking details, etc.
Cybercriminals later use this personal data for their malicious purposes which can lead to serious privacy violations, financial loss or even identity theft.
Malicious computer viruses and ransomware like Cryptolocker, ILOVEYOU, RaaS, Melissa, and Emotet are some of the famous and latest threats to your PC.
Today, in this blog, we will discuss about the latest computer viruses to help you understand their behavior so you can neutralize them before they cause any harm to your system.
How to Stay Secure from a Computer Virus Attack?
The best way to stay safe and secure from malicious and recent computer viruses is to use an advanced antivirus protection suite. In addition to this, using a malware removal tool is also strongly recommended.
These programs create a protective shield around your PC against the deadly threats like malware, viruses, ransomware, trojans, worms, PUPs, rootkit, browser hijackers, etc.
Top 25 Latest Computer Viruses 2020 You Must Not Overlook:
Threat of the Month: COVID-19 Malware
Cybercriminals and black hat hackers are recently found taking the advantage of current outbreak of the coronavirus disease to distribute new COVID-19 malware to the security vulnerable systems.
After successfully invading the targeted computer, it silently rewrites the system’s master boot record (MBR) and wipes out the entire stored data without the knowledge of its owner.
This coronavirus-theme malware strain is designed with a sole intention to cause destruction to the millions of infected machines all across the globe.
Cybercriminals are constantly evolving new tactics to make their malware more adaptable, resilient and damaging than ever to exploit system and network vulnerabilities. Take a look at some of the top cybersecurity threats:
1. CryptoMix Clop Ransomware
It is the new variant of a well-known CryptoMix ransomware family that aims to exploit the whole computer network instead of individual users. Cybersecurity researchers discovered this variant at the end of February 2019. After gaining persistence in the targeted system, this vicious ransomware encrypts all the stored files by appending .CLOP or .CIOP extension to the end of all victim’s file names.
Whenever the victims’ tries to open an encrypted file, it displays a ransom note informing the users about the attack and compels them to pay the ransom amount in Bitcoin or other cryptocurrencies for the alleged restoration of their encrypted files.
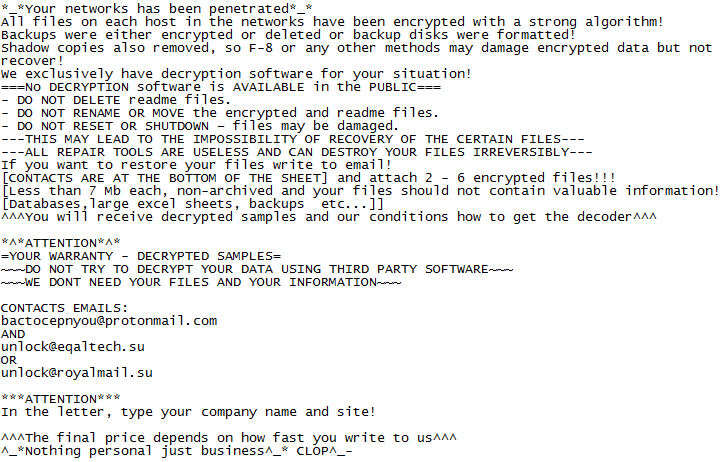
Image Credit: Malware Hunter
Read More: 15 Best Free VPN For Windows 10
2. Gandcrab Ransomware
GandCrab, one of the most destructive ransomware crypto viruses which was first introduced in January of 2018. GandCrab family variants have been employing various distribution techniques such as Fallout exploit kits, malicious URLs, keygens, GradSoft, RIG, etc. to make an entry into targeted computers.
Once executed, it terminates all the active tasks and processes running on the system and starts encrypting all kinds of files and folders available on your hard drive. Also it appends .GDCB extension to the end of all file names and displays a ransom message CRAB-DECRYPT.txt with instructions regarding the payment method.
Creators of such infections use advanced AES–256 and RSA-2048 encryption methods and store the decryption key on command and control servers hosted on .bit domains.
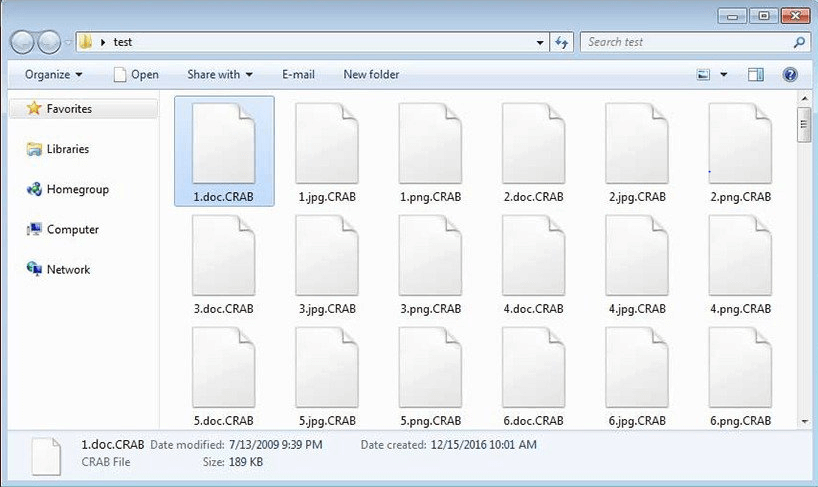
3. Trojan Glupteba
One malicious program that should never exist in your computer is Trojan.Glupteba as it has a tendency to bring several other malicious programs with itself. Cyber criminals often distribute the Trojan.Glupteba infection through exploit kits.
The primary purpose of this latest computer virus is to redirect the users to malicious and third-party sites so that it can download and install more harmful software. Mostly the malware infection enters as a service on the affected Windows system and authorizes various processes on the system by masquerading as a legitimate or authentic software.
After doing this, it gathers users’ data for various IP addresses and then generates the traffic by routing the users towards several malicious domains such as sportpics.xyz, bigdesign.website, kinosport.top, ostdownload.xyz, etc. To prevent such threats, avoid visiting unsafe websites, downloading junk attachments and enable your popup blocker.
4. Cyborg Ransomware
Aids Info Disk Trojan (AIDS), also known as the PC Cyborg ransomware virus, was the first of their kind, introduced via floppy disk back in 1989. The malicious program was designed to count the number of times the operating system of a computer turned on, once the tally reached 90, it used to encrypt all the victim’s data and change the desktop wallpaper with ransom message Cyborg_DECRYPT.txt.
The ransom note informs the victims about the encryption and asks for a huge sum of money in return if they want to decrypt their files. In addition, recently cyber crooks used an executable file disguised as a .jpg image format to distribute the variant of Cyborg through a fake Microsoft Windows 10 update.
To protect yourself from this ransomware, never click or download any kind of attachment files with .jpg extension coming from an unknown or unsolicited sender.

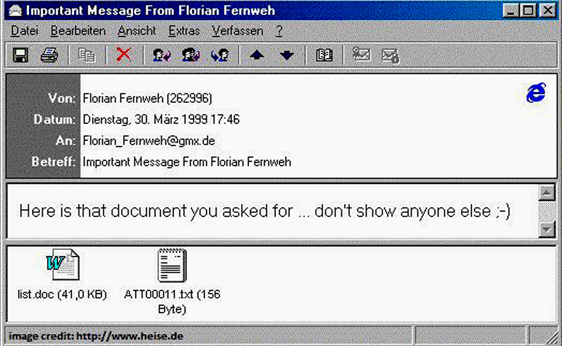
5. Melissa Virus
The Melissa was one of the most dangerous macro viruses, developed by a software programmer named David Lee Smith back in March, 1999. The virus was distributed through an e-mail attachment titled list.doc. When the users opened the document with Microsoft Word, the Melissa virus was injected onto the victim’s computer.
It was specifically designed to take control of the victim’s Microsoft Outlook program and then mass mail itself to another 50 individuals present in the user’s mail list.
6. ILOVEYOU
ILOVEYOU, also known as the Love Bug, is one of the deadliest computer worms that exploited more than 10 million systems since it was first discovered in May, 2000. Hackers distributed it via an email message with a document titled as “LOVE-LETTER-FOR-YOU.txt.vbs”.
Upon clicking the interpreted file, it executes the Visual Basic script and starts overwriting a wide array of stored files, including Microsoft Office, media files, and backup files. And then it makes the most of the vulnerabilities of Microsoft Outlook by mass mailing a copy of itself to all other recipients available in the Windows Address Book.
It allowed malware authors to cripple millions of internet-connected systems and due to the fact many governments and large organizations around the world were forced to shut down their mail delivery systems.

Image Credit: Wikipedia
7. Storm Worm
Storm Worm is another dreadful Trojan horse which was first dubbed by the company named F-Secure in the first month of 2007. The malware attack began affecting hundreds of computer using Windows operating systems through an email message with following subject lines:
- 230 dead as storm batters Europe.
- War with Iran is the reality now.
- Occupation of Iran.
- Naked teens attack home director.
- A killer at 11, he’s free at 21 and kill again!
When the user clicks on such attachments, the Storm Worm activates the wincom32 service and downloads several other malware-infected software, turning the compromised system into a bot or zombie computer. In addition, the hackers behind such attacks can remotely control the botnet and further use it to send spam messages and viruses to other computer users.
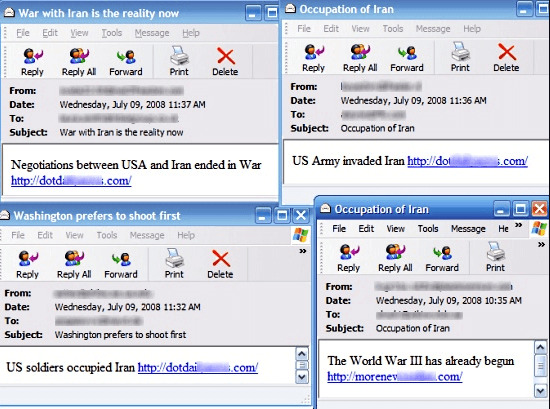
Image Credit: Wikipedia
Read More: 13 Best File and Folder Lock Software For Windows 7, 8, 10
8. Emotet Malware
Emotet, also known as the Mealybug, is an extremely harmful banking Trojan that acts as a downloader of other malicious programs. Emotet malware is one of the most dangerous malware threats of 2019.
Recently cybersecurity researchers discovered that hackers are now exploiting the fear of global epidemic Coronavirus to spread Emotet malware through malicious email attachments in Japan.
The spam email messages claim to provide the latest information about the outbreak of the Coronavirus and once the users clicks on the document, the Emotet malware gets installed onto their computer. After gaining access to the victim’s computer, it steals both personal and financial information and later trades it on the dark web marketplace.
9. B0r0nt0k Ransomware
A new cryptovirus of ransomware family called B0r0nt0k is targeting thousands of Linux and Windows web servers and encrypting all of the available files with an advanced cipher algorithm.
Instead of directly locking them, the ransomware places .rontok extension at the end of file names. Unlike other ransomware viruses, it makes false entries in the Windows registries, modifies various start-up and browser settings, disables security programs, and locks down the entire system.
The sole purpose of developing such dreadful file-encrypting malware is to extract a hefty amount of ransom money from innocent computer users. And if the victim fails to pay the ransom within a given time, the attacker deletes all the stored files and folders permanently.
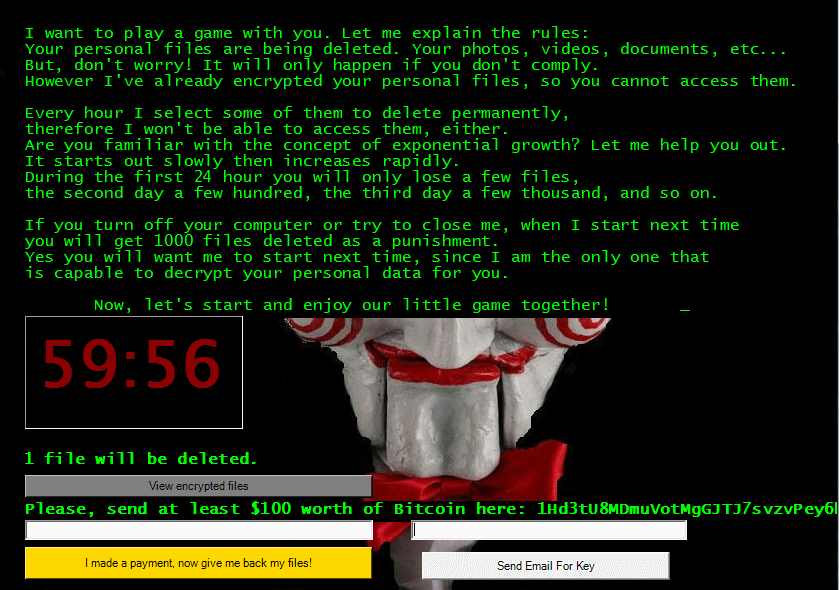
10. Jigsaw Ransomware
Jigsaw is one of the most dangerous and well-known ransomware families with hundreds of variants of the malware. Cybercriminals often distribute this type of malicious program via junk attachments, free software updates, pirated movie download links, unsafe third party domains, etc.
After successfully invading the targeted system, it encrypts the victim’s files with extensions such as .Fun, .Beep, .FuckedbyGhost, .Game, etc. After doing this, it shows a ransom note which contains information about the payment method and threatens to delete some files permanently every hour if the user fails to transfer the money within a given time period.
However, a company named Emsisoft is now claiming that they’ve managed to develop a decrypting tool for Jigsaw ransomware variants.
11. Thanatos Ransomware
It is another highly dangerous malicious computer virus that belongs to a ransomware family called Thanatos. Similar to other cryptovirus, it encrypts the user’s data and appends .THANATOS extension at the end of each compromised file name. For example, file named luck.txt will be encrypted and renamed to luck.txt.THANATOS.
After encrypting, it starts blackmailing victims’ by not allowing them to access their files until they pay the ransom amount demanded by the attackers. It is suggested that you should never trust such cybercriminals because once you paid the ransom amount, there’s no guarantee that you would be able to retrieve the lost or encrypted files.
To keep your system secure from such harmful malware infections, it is recommended to install a good antivirus program so you can protect yourself from any future computer virus attacks.
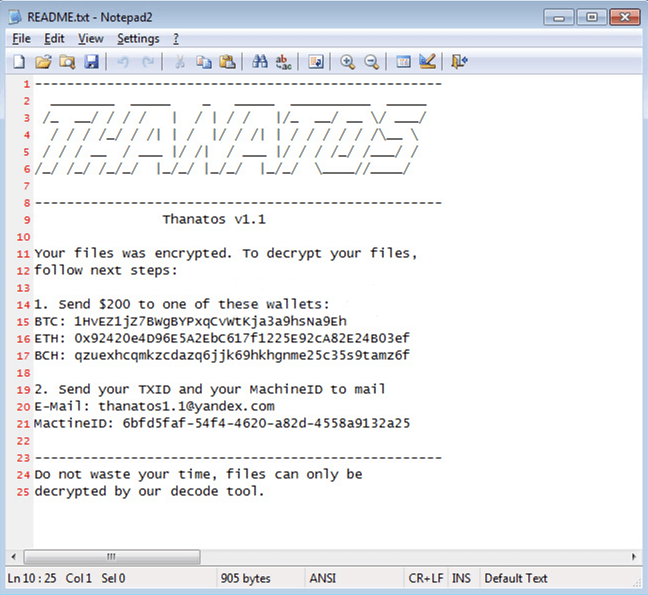
Image Credit: iobit
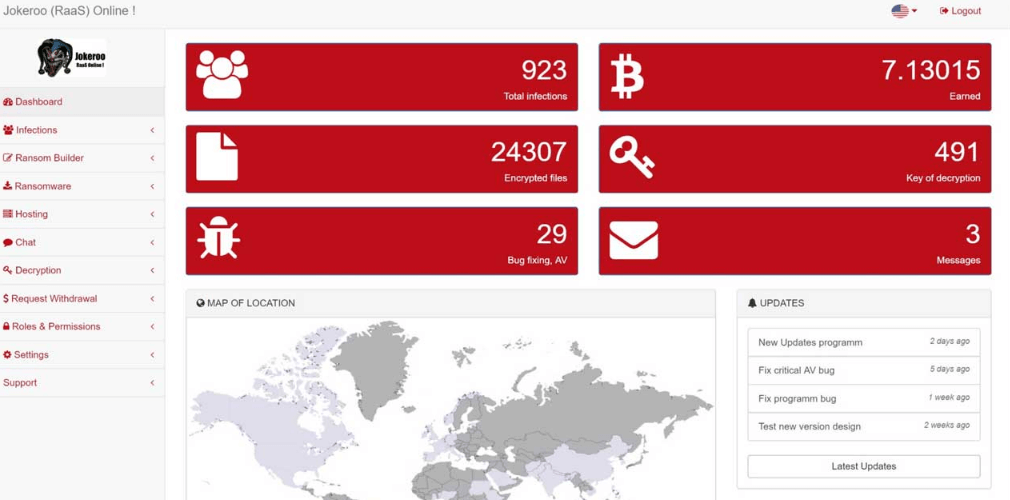
12. Jokeroo
Jokeroo is one of those recent computer viruses that cybercriminals are now using as ransomware-as-a-service (RaaS) to offer various membership packages with compact malicious kits to launch ransomware attacks.
Hackers are promoting Jokeroo RaaS via Twitter and on various underground hacking forums, allowing other people to become an affiliate, distribute the ransomware, and then split the ransom amount that they would receive from the victims.
To keep your data and online identity secure, it is recommended to avoid clicking suspicious websites, pop-up ads, junk attachments, etc. and make sure that all your security programs are up and running.
13. Gameover ZeuS
GameOver Zeus (GOZ) is a peer-to-peer (P2P) credential-stealing Trojan-malware of the Zeus family that also acts as a downloader and dropper of the CryptoLocker ransomware.
The cybercriminals started spreading Zeus malware through phishing and spam email campaigns and once injected to the target system, they constantly monitor or control its activities via command and control servers.
After gaining access to the victim’s computer, the malware steals the user’s financial details, including username, passwords, credit card information, etc. Apart from that, scammers used it to download and launch other malicious executables and hide essential confidential files in order to make profits via blackmailing innocent users.

Read More: 12 Best Privacy Apps For Android in 2020
14. GoBrut
GoBrut is one of the latest computer viruses that made its first appearance in March, 2020. This new emerging malware threat is written in the Golang programming language with the sole intention to cause damage on thousands of Linux and Windows-based machines.
Even though the malware is in its early stage of development, it is still capable of exploiting the vulnerabilities of the computers running without the proper antivirus program or using weak passwords. Thus, it is extremely important to use a strong and hack-proof password along with an updated antivirus suite to prevent such kinds of dangerous malware attacks.

15. MyDoom
The Mydoom worm, also referred as the W32.MyDoom@mm, Shimgapi and Novarg, is the fastest-spreading virus, surpassing earlier records set by the ILOVEYOU malware.
Mydoom computer was first surfaced in January, 2004 and distributed via mass mailing with subject lines such as transmission error, test, mail delivery system, message could not be delivered, etc. in many different languages.
When the user downloads the attachment, the worm gains access to the victim’s system and resends itself to more people found in the user’s contact lists.
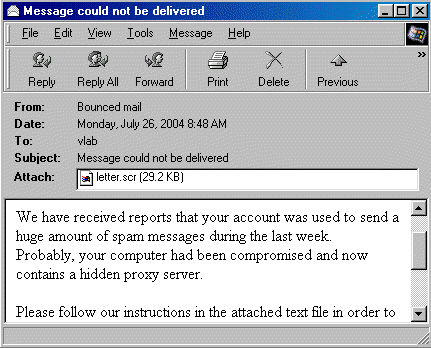
Image Credit: Computer Virus
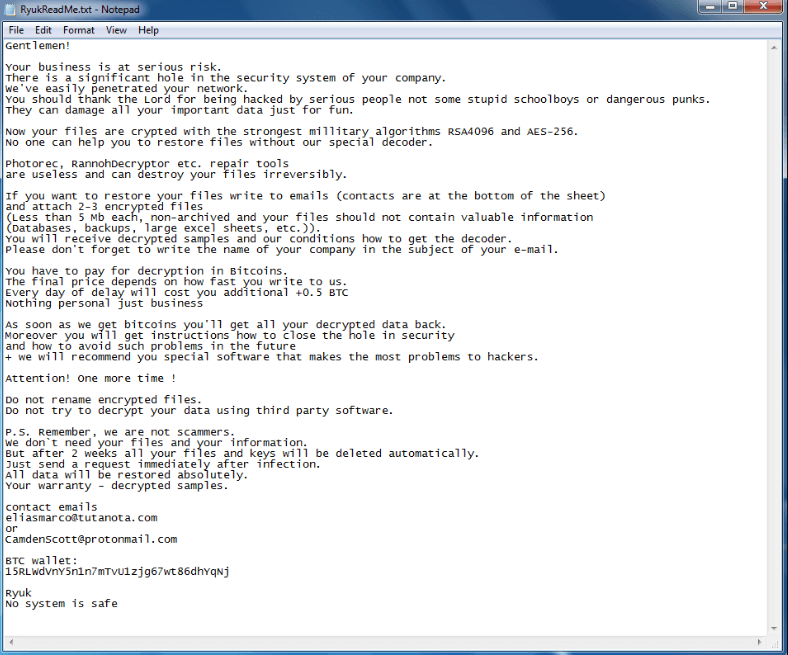
16. Ryuk Ransomware
Ryuk ransomware is one of the most lucrative ransomware attacks being witnessed by the large organizations and high-profile business leaders today. The ransomware is operated by a threat group named WIZARD SPIDER that focuses on infiltrating the computer networks of the large group of companies so that they could get a large sum of ransom amount in exchange for their encrypted data.
The hackers behind such ransomware attacks use strong encryption algorithms such as AES-256 and RSA-4096 to encrypt the files which means using any other free decryption tools available online would not be able to help you retrieve your data.
According to recent reports, the ransomware is now exploiting the fear of the global Coronavirus epidemic and targeting large health organizations and other healthcare facilities to trigger high-value malware attacks.
17. Astaroth Trojan
Astaroth Trojan is one of the recent malware threats that is capable of stealing both personal and sensitive information such as login credentials, passwords, credit card details from the compromised system without the knowledge of its owner.
This information stealer is typically delivered via massive spam campaigns in Brazil and some parts of Europe near the end of 2018. The Astaroth Trojan malware poses a dangerous threat to security of all operating systems. Therefore, never click on spam emails from unknown senders because it may contain harmful modules of various malware infections.

18. LockerGoga Ransomware
The LockerGoga ransomware is one of the nastiest cryptoviruses that made its presence felt when it attacked the systems of one of the largest aluminium manufacturer companies worldwide, Norsk Hydro.
Unlike other ransomware families, the main objective of LockerGoga ransomware is to cause damage and disrupt general operations. Once injected into the targeted system, it locks the victim out of the compromised computer by changing the credentials of its accounts.
The only way to keep yourself safe from this ransomware is to keep your Windows OS and security programs updated at all times.
19. Sasser & Netsky
Sasser & Netsky are two dangerous computer worms developed by a 17-year-old student of computer science, Sven Jaschan. The Sasser worm was designed to scan the random IP addresses and exploit the PCs running on vulnerable versions of the Windows 2000 and Windows XP operating systems.
Whereas the Netsky was designed to spread via mass email campaigns. However, it is really easy to neutralize the effects of such computer worms, all you need to do is update your system through Windows Update and you’re your firewall properly configured.
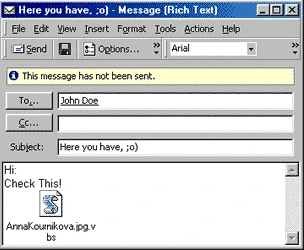
20. Anna Kournikova
The Anna Kournikova virus is another computer worm created by a 20-year-old student named Jan de Wit in February, 2001. The worm was designed to entice users into clicking a picture of the well-known tennis player Anna Kournikova, distributed via spam email attachment titled as “Here you have, ;0)”.
Upon clicking the message, it installs a malicious VBScript program which would then auto-send itself to other contacts available in the victim’s address book. However, the computers running on Linux and Macintosh operating systems were not affected by this dangerous computer virus.
Read More: 11 Best Free Adware Removal Tools For Windows
21. CDPwn
One of the latest computer viruses in 2020, CDPwn is a combination of five extreme, zero-day vulnerabilities discovered by cybersecurity researchers in the Cisco Discovery Protocol (CDP). Cisco Discovery Protocol acts as a data link layer and obtains info about the associated Cisco equipment.
In addition, the five CDPwn vulnerabilities can allow remote attackers to take control of millions of Cisco devices such as routers, cameras, switches, IP phones, firewalls, NCS systems.
Four of the five vulnerabilities are remote code execution (CVE-2020-3119, CVE-2020-3118, CVE-2020-311, and CVE-2020-3110) whereas one is a Denial of Service vulnerability (CVE-2020-3120).

Image Credit: Help Net Security
22. Stuxnet
The Stuxnet Worm was originally developed by the United States in collaboration with the Israel government with the sole intention to cause substantial damage to Iran’s nuclear facilities.
However, neither government has taken the responsibility of such actions, the malicious computer virus appeared to take control of Iranian supervisory control and data acquisition and programmable logic controller systems to cause damage to gas and nuclear centrifuges.
As a result, the Stuxnet virus attack reportedly ended up infecting Iran’s thousands of industrial control systems.
23. Conficker
Conficker, also referred as the Kido and Downup, is the largest computer worm, infecting more than 9 million Windows computers in over 190 countries since its first ever appearance in November, 2008.
It exploits the vulnerability of Windows operating systems and turns the compromised machine into a botnet to launch high-profile distributed denial-of-service attacks (DDoS), steal victim’s data, run spam campaigns, etc.
To protect yourself from such computer worms, keep your Microsoft Windows software and other programs up-to-date.

Image Credit: F-secure
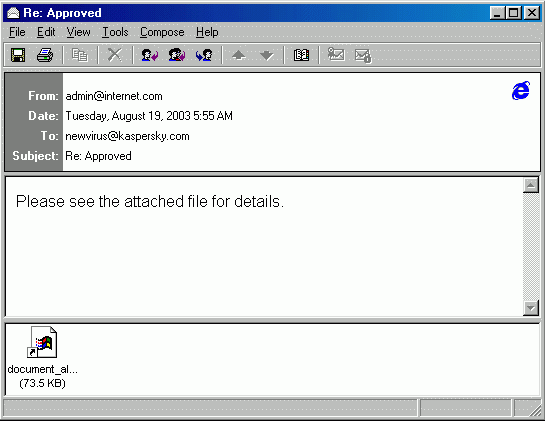
24. Sobig
The Sobig worm, classified as a type of computer malware, infected millions of internet connected devices running on Microsoft Windows operating systems.
Similar to other computer worms, it was distributed via spam email with one of the following subject lines:
- Re: Details
- Re: Thank you!
- Re: Approved
- Re: Your application
- Your details
- Re: Wicked screensaver
- Re: That movie
The email message was also appeared to contain a document by one of the following titles:
- document_all.pif
- your_details.pif
- movie0045.pif
- application.pif
- document_9446.pif
- wicked_scr.scr
Once users open the attachment, the worm gets installed on the system and starts forwarding itself to other email addresses available in the victim’s computer. To prevent such dangerous computer viruses from entering into your system, avoid clicking on the spam email messages and run its attachments that are coming from the unsolicited sources.
25. Kuik Adware
Kuik, an advertising-supported software, commonly known as the ‘Adware’, is now infecting Windows users by masquerading itself as a legitimate update of Adobe Flash Player.
Developers of such programs are dropping Kuik adware in three different segments that are documented as legitimate flash player, upp.exe file, and certificate. After gaining access to the victim’s computer, it builds connectivity and adds the domain name system (DNS) 18.219.162.248 to all established network interfaces.
After doing this, it gathers all the victim’s data, including financial details and sends it to the hosting server named ‘kuikdelivery.com’. And once the domain server acquires the victim’s data, Kuik adware triggers other malicious programs such as harmful chrome extensions, coin miner applications, etc. on the compromised system.
Having talked about the most dangerous and latest threats to your PC, below are the top trending cybersecurity attacks and newest computer viruses that you need to protect yourself from in 2020.
The Top CyberSecurity Trends & Latest Malware Threats of 2020 You Need to Watch Out For:
1. Hackers Abusing WordPress Sites to Deliver Backdoor Malware
Hackers are recently found exploiting the vulnerabilities of one of the most popular content management systems, WordPress to distribute backdoor malware to news blogs and corporate websites. As per cybersecurity expert reports, the malware was disguised as the legitimate Google Chrome update with the intention to drop other payloads such as Trojan, information stealers on sites based on WordPress CMS.
2. Rapid Surge in IoT Device Attacks
As we become more dependent on IoT (Internet of Things) devices such as video doorbell cameras, speakers, alarm clocks, we can see a massive growth in IoT-based attacks. The number of internet-connected devices doesn’t come with a strong in-built firewall security, leaving them vulnerable to large scale attacks.
As per the researchers report, almost 98% traffic of IoT connected devices worldwide is unencrypted, putting the privacy and confidential data of the users at stake.
3. Operation ShadowHammer That Leveraged Asus Live Update Software
ShadowHammer, a supply chain attack that allowed cybercriminals to hijack the Asus live update utility software and distribute a secret backdoor malware to millions of compromised machines.
4. Hackers Using Fake Bitcoin QR Code Generator to Steal $45000
Bitcoin QR code generator allows users to convert their Bitcoin address to a QR code for quick and easy money transfers. Recently cyber thieves or scammers have managed to create a malicious barcode generator to steal 7 BTC (Bitcoins) worth of approx. $45000 from the victims.
So, if you own some bitcoins or any other types of cryptocurrencies, think twice before making any payment through BTC to QR Code websites.
5. Android Banking Trojan Gustuff Stealing Money From Your Bank Account
Another banking Trojan known as Gustuff has targeted more than 130 Android banking, messaging, and cryptocurrency applications. These applications open the door for hackers to get into your smartphone and steal your financial details and transfer money out of your account.
Popular targeted bank, messaging, and payment apps include Bank of America, J.P.Morgan, PayPal, Walmart, WhatsApp, Skype, and many others.
6. Phishing Attack: Fake Covid-19 Antivirus to Install Backdoor Malware
Phishing is by far one of the most common and top cyber threats that you need to be aware of in 2020. In light of this, security experts have recently discovered a few websites that are taking advantage of the global COVID-19 pandemic to target computer users using a fake ‘Corona Antivirus’ software.
This fake antivirus solution claims to provide physical protection to users through a Windows application. When users fell for the bait, it injected a malware payload and turned the victim’s system into a botnet by using a BlackNET RAT (remote access Trojan).
7. Cyborg Ransomware Found in the Windows Update
Cybersecurity experts have recently uncovered a malicious spam campaign that informs the targeted users about a ‘critical Microsoft Windows update’ and upon clicking the message, it infects the victim’s machine with Cyborg ransomware.
It is suggested not to open or run email’s attachment claiming to be from Microsoft regarding a new Windows update.
8. WinRAR Bug is Being Exploited to Inject Malicious Payloads
With more than 500 million active users, WinRAR is one of the world’s most popular file archiver utility software for Windows available in the marketplace today. Recently security researchers have discovered a 19-years-old WinRAR code-execution flaw that hackers are exploiting to trigger dangerous malware attacks on Windows machines.
Therefore, it is recommended to keep your WinRAR application updated to avoid such harmful infections.
9. Ransomware-as-a-Service (RaaS) Attacks are on the Rise
With each passing year, ransomware attacks are increasing at an alarming rate. RaaS aims to provide malware exploit kits to other people who want to carry out sophisticated attacks but don’t have the sufficient knowledge of coding. In short, it offers everything a novice hacker needs to unleash ransomware attacks on businesses.
10. Hackers Stealing User’s Credentials Via Password Managers
Recently many cybersecurity experts reported a vulnerability in popular password managers due to which cybercriminals started gaining access to the users’ credentials stored in the password encrypted vaults. The security flaw also left them vulnerable to PIN brute force attacks.
So, these are some of the trending threats of 2020 from which you need to protect your computer. Now, below take a look at the best security practices and tips that can help you prevent them:
Tips to Prevent Dangerous Malware & Computer Virus Attacks In 2020:
Your computer is susceptible to many highly dangerous malicious computer viruses. To neutralize them, it is important to keep yourself ready against such intrusions. Below we’ve listed all the necessary web practices and prevention tips that you should follow to stay safe and get the best, trouble-free PC experience.
1. Get the Best Antivirus & Anti-Malware Software for Your PC
Nowadays, the latest computer virus and malware infections poses a dangerous threat to your system, financial data, and even online identity. Therefore, it is essential to have an antivirus protection suite and an anti-malware tool to keep your system safe from the latest malicious threats.
2. Always Keep Your Windows OS & Other Programs Updated
An outdated version of an operating system or a program could be the hacker’s doorway to your computer. Thus, it is important to keep your system updated through Windows update at all times. By doing this you can protect your PC from virus attacks.
3. Be Cautious About Downloading Third-Party or Freeware Software
Try to avoid third-party download or visiting suspicious sites that offer freeware because they often come bundled with other malicious programs.
4. Don’t Click On Any Pop-up Ads & Things Shouting About Free Rewards
While browsing a website you must have come across numerous online ads that pops up out of nowhere. Cybercriminals often use those tempting advertisements to provoke users to click on them, i.e. spin the wheel to win a brand new iPhone X.
Never respond to such luring offers and popups in any way. Simply close the site by clicking on the ‘Close’ icon at the upper right corner.
5. Beware of Spam Email Attachments from an Unknown Source
It’s 2020, but still cybercriminals greatly depend on spam and junk email attachments to trigger virus and malware attacks. So, avoid opening any suspicious or spam emails from an unknown sender that asks you to download and run its attachment.
6. Always Use Strong and Hack Proof Passwords
Using weak and easy-to-crack passwords is just like giving your house keys to a thief. Therefore, it is recommended to use a strong and unique password that is easy to remember and hard to guess. Also, turn on multi-factor authentication whenever available.
7. Take Regular Backup of Your Files
Regularly backing up your computer can help you keep your valuable data safe from prying eyes. Therefore, it is suggested to take a regular backup of your important files to an external or cloud drive to prevent any kind of data loss problems.
8. Enable Your Microsoft Defender Firewall
If your device is connected through a network or the Internet, it is important to keep your Windows firewall turned on to prevent cybercriminals and malicious programs from gaining access to your system.
Writer’s Tip: If you find a suspicious file on your system, you can upload it on the VirusTotal website and see if it contains any kind of virus and malicious content. VirusTotal, a subsidiary of Google’s parent company Alphabet Inc., is a free online service that aggregates dozens of top antivirus applications to help you analyze suspicious URLs and files in the most efficient manner.
That’s all folks! These were some of the most dangerous malware and latest computer viruses of 2020. The best way to protect yourself from such malicious threats is to use an updated antivirus program along with a powerful anti-malware tool.
Apart from that, follow all the aforementioned prevention tips and online safety practices to keep your system secure and safe, always.


