Cyber Security
Gcore Web Application Security, Pricing and Features
Web applications are necessary for the functioning of companies within the virtual age, serving as gateways for purchaser...
6 Best Nord VPN Alternative You Should Use in 2024
Best alternatives to Nord VPN ensure online safety at a minimum price (some of them are even free) with a fast connection and...
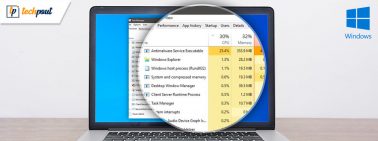
How to Fix ‘Antimalware Service Executable’ High CPU Usage
The Windows security process called Antimalware Service Executable sometimes consumes more than expected resources, degrading...
How Faiq Farooq is Single-Handedly Upbringing Cybersecurity Industry
Digital attacks are getting more and more common by the day. Digital threats from hackers, ransomware developers, and other...
Is “[email protected]” Legit and How to Prevent this on Instagram
Phishing on Instagram has been reported by many users lately. It involves direct messages or emails that look like coming...
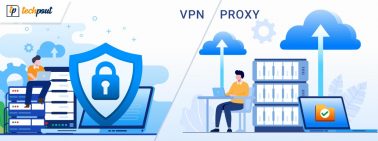
Difference Between VPN and Proxy Server | Proxy vs VPN
In this article, you will find different points of difference between proxy and VPN to clear the concept, working, and other...
What is a Network Security Key
Read out the complete article to learn everything you need to know about network security key Windows 10, 11, or older version...
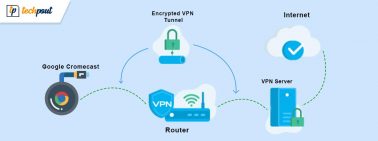
How to Set up VPN on Chromecast
If you want to know how to set up a VPN on Chromecast and surf anonymously, then everything explained in this article will help...
What is Computer Security | Common Computer Security Threats
Read on to get detailed knowledge about computer security, safety risks, and how to protect your computer.Your computer plays...