What is a Network Security Key

Read out the complete article to learn everything you need to know about network security key Windows 10, 11, or older version devices.
Are you setting up your WiFi or troubleshooting it and are unable to find your network security key to proceed with establishing the network connection? Don’t worry you are not alone. Some users also questioned the same i.e is the network security key the same as a password? Simply put the network security key or your Internet security key is nothing but the password of your WiFi.
The network security key is a particular type of key that enables communication between the router and the device. It provides a secure internet connection to the connected device. But that’s not it. There’s more on the plate when it comes to the security key on the router. Stick through the write-up till the end and you will have answers to all the questions related to the Network security key.
What is a Network Security Key on a Laptop or Computer?
The term network key has gained popularity in recent times. There are different network keys that work for several devices. It is important to know and understand the type of Network security key used by your router to resolve the issue and set up the router for an uninterrupted network.
Below are the three types of Network keys
1. WEP
Wired Equivalent Privacy is a security standard that allows protection same as that of wired networks. It was ratified in 1999 & retired in the year 2004. However, there exists an option to use the standard now also.
Despite advancements from 64-bit to 128 & 256-bit encryptions the risk of security in WEP increased. As the security key in the WEP could be cracked with simple software. But due to the possibility of this network key type being compatible with the older version devices, it is still in use. The type is vulnerable to various cyberattacks and is one of the least secure options available for network types.
Also Read: What is Computer Security | Common Computer Security Threats
2. WPA
WiFi Protected Access came into action in the year 2003 to resolve the vulnerabilities in the WEP network. The advancements offered by WPA included various checks at the security level to save the data from getting intercepted by the attackers.
However, the issues of advanced Encryption standards missing from the network type arrived over time in WPA.
3. WPA2
With Advanced Encryption Standards, WPA2 was launched in the year 2006 to overcome the shortcomings faced by the users of WPA. The only vulnerabilities known for WPA2 are associated with large businesses and should not be a concern for users with the home networks.
It is advisable to pick WPA2 over the outdated method for network security to access your WiFi.
How to Find Network Security Key?
The location of your Network key varies depending upon the type. There’s no specific answer to the question of where is the network security key on my router. For most of the network types, the keys are written on the paper that is provided by the network owner. However, for some routers, WPA or WPA2 keys are printed on the stickers at the sides of the router.
If you are using your Smartphone as a personal hotspot to access the internet on the other device you can find or set up the password in the Settings of your mobile. For iPhone users, the network security key for hotspot can be found by enabling the feature of Keychain present in the iCloud Settings menu.
As you plan to set up your router for your device and personal use make sure you set up a strong password that can be easily remembered yet strong.
Also Read: Cybersecurity & Personal Data Protection Tips to Stay Safe
How to Create a Strong Network Security Key?
There are no set rules for setting a strong password or network security key, but experts suggest while setting up your network security code keep in mind the following standards
- It must have 12 characters ( or more).
- Use combinations of letters, numbers, and symbols.
- Don’t use the basic substitutes (such as zero for 0).
- Avoid using the path of your keyboard keys (eq: qwerty, zxcvbn, etc)
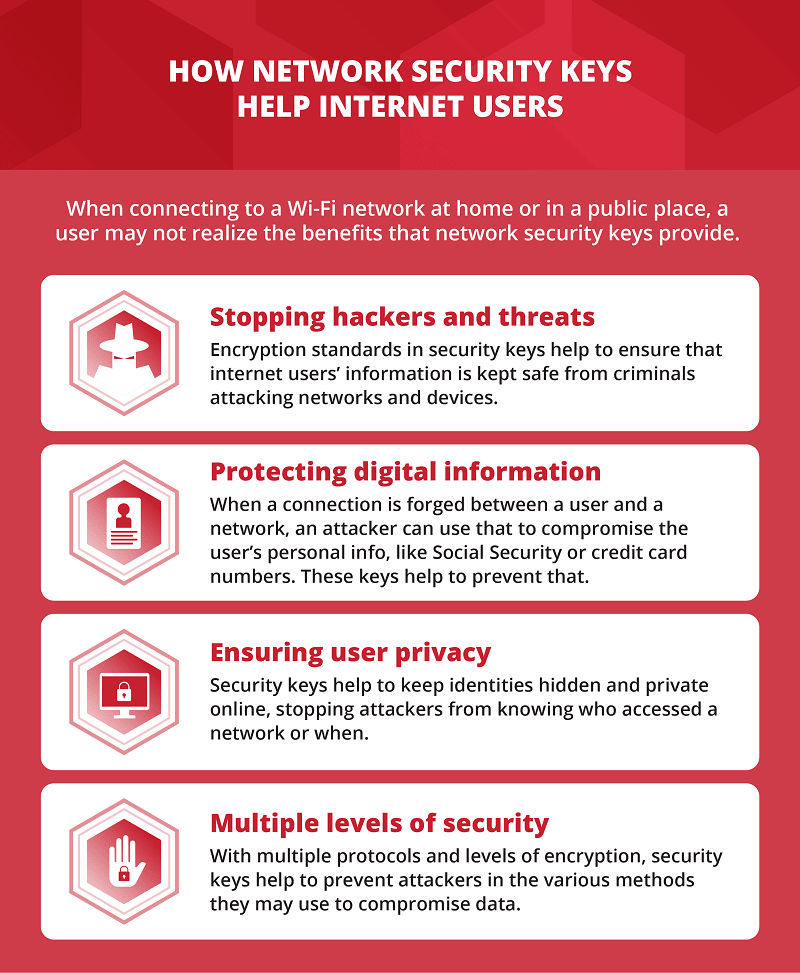
How do Network Security Keys Protect the Users?
As we connect to different networks at our home, workplace, or sometimes even in public places these network security keys WiFi offer the following benefits to the users:
- These network security keys help you stop cyberattacks and prevent your data from possible threats. The Encryption standards that are provided by these keys ensure the safety of all the information of users from any criminal attacks.
- As you connect to a network the attacker can use the connection to leak personal information like Credit card details, social security, etc. The network security keys ensure that all your data is safe.
- The privacy of a user is also kept intact by using these network security keys. Your personal identities are not disclosed online and remain hidden to keep your information unavailable to the attackers.
- As the keys are equipped with multiple protocols, the security levels are also multiplied making the connections secure and inaccessible for the attackers to overcome the possibility of compromising data.
Also Read: Cyber Security Threats to Small Businesses
Closing Lines on Network Security Key:
Hopefully, the above tutorial helped you understand the complete concept of the network security keys and their types. Now that you know the exact network security key meaning and where to find the network security key on the router you can access the internet in different networking environments. The network security keys are important as they are the first step to defense when it comes to cyber-attacks. Understanding its working and the need to set up a strong password will help users and professionals in keeping their data safe.
We hope the write-up helped you connect the dots and address your concerns. Feel free to raise your queries in the comments below. Also, make sure you sign up for our blog to never miss our posts and get the latest updates delivered to your mailbox. Follow us on Facebook, Twitter, Instagram, and Pinterest.